Pre-Installation Checklist
Make sure you have all of the following steps in place before
you setup Exchange Server 2010 on Windows Server 2008 R2 64 Bit.
For simplicity we are assuming you are setting up a small office where
one machine will be used for both the Active Directory and the Exchange
Server. This setup works just fine and reduces the number of machines to
maintain. If you have a larger office you may want to consider separating
the Active Directory machine and the Exchange 2010 Server.
Install Windows Server 2008
R2 64 bit version
Exchange 2010 is a 64 bit application and requires 64 bit versions of
Windows Server 2003 or Windows Server 2008. You should select a
computer that is capable of running the 64 bit version of Windows Server
2003 or 2008. For this example, we will start with a clean
installation of Windows Server 2008 R2 64 bit version that has not had any roles
installed.
After installing Windows Server 2008 R2 we set the clock and the name of
the server to be "EX2010". At this point this server is configured
to be a stand alone computer with default settings.
 Configure Your Static IP Address
Configure Your Static IP Address
The default installation of Windows 2008 sets your IP v4 and IP v6
addresses to use DHCP. Since we will be configuring this computer
to be a domain controller, you must change the IP address of the computer
to be a static IP address.
To change your IP address, click on "View Network Connections" in the
Server Manager screen. This will display the list of active
network interfaces.
Double click on your network adaptor to display the adaptors status.
Press the Properties button.
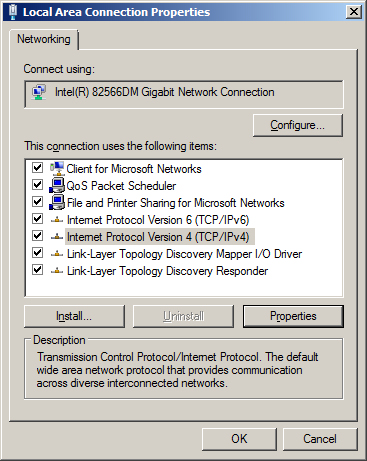
Highlight "Internet Protocol Version 4 (TCP/IPv4)" and then press the
Properties button.
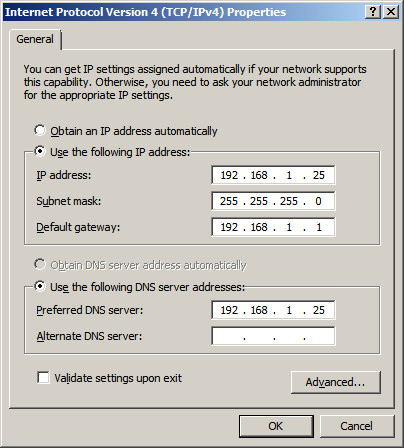
Change the radio button to "Use the following IP address" and enter
an IP address you want to use for this server. In our example, we
chose to assign this server the internal IP address "192.168.1.25".
We also have a firewall appliance that operates as a gateway at the IP
address "192.168.1.1".
NOTE: It is important to include this computer in the DNS list.
You should list the IP address of this computer as the first entry in
the list of DNS servers. In the alternate DNS servers field, enter
the IP address of a DNS server provided by your ISP.
Press OK to save your changes.
Now you will need to modify the support for IP v6. If your
network uses IP v6, then you will need to select "Internet Protocol
Version 6 (TCP/IPv6)" , press the Properties button, then enter a
static address. If you are not using IP v6, you can leave the IP v6
set to the default setting of DHCP.
NOTE: Exchange requires that IP V6 be
enabled. Even if you do not use IP V6 you must leave it enabled.
During the setup of Active Directory, the Active Directory Setup Wizard
will check that both IP v4 and IP v6 have static addresses. As long as
the IP v4 address is static you can continue the installation. DO
NOT DISABLE IP V6 or else the Exchange Hub Transport Service will not
start.
At this point you should have all IP addresses on this server
configured as static IP addresses. OR you have the IP v4 address
configured as static and the IP v6 configured using DHCP. Press OK to save your changes and close
the Network Connection screen.
Activate Auto Update
The next step in making this server a Domain Controller is to
activate auto update. Active Directory will not install until this
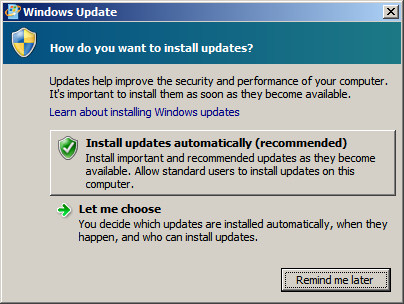
computer has auto updates active. To activate auto updates, click
on the link "Configure Updates" and then select the
option to have Windows automatically install updates. At
this time Windows will download updates and will most likely need to
reboot your computer. Allow the updates to be applied and the
computer to be restarted until all updates are applied
before installing
Active Directory. You do not want to be in the middle of
installing Active Directory when an auto update needs to reboot your
computer.
 Add role - Active Directory Services
Add role - Active Directory Services
The process of installing Active Directory consists of two steps: the
first step is to install Active Directory and the second step is to
configure your Active Directory. Once this is complete, your
Windows Server will now be a Domain Controller.
Step 1 - Install Active Directory
At the Computer Management Screen, press the "Add Roles" link.
At the Select Server Roles dialog, check/tick the option "Active
Directory Domain Services".
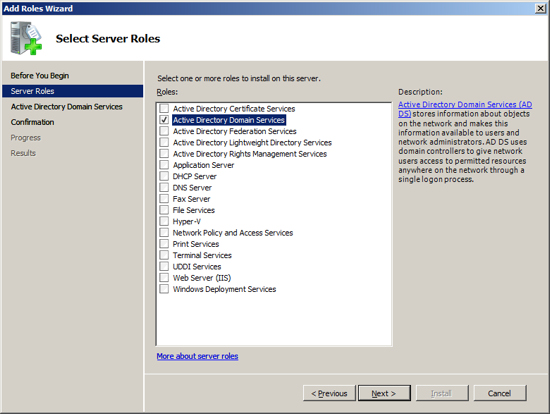
When you select Active Directory the Select Server Roles Screen will
inform you that you also need to install the feature ".NET Framework
3.5.1". Press the "Add Required Features" button.
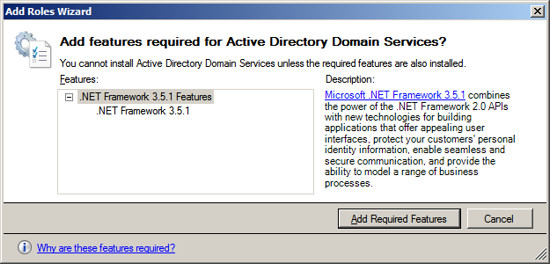
After acknowledging the required feature, press Next.
Active Directory Domain Services will present information about the
changes it will make to your server. Review this information and
press Next.
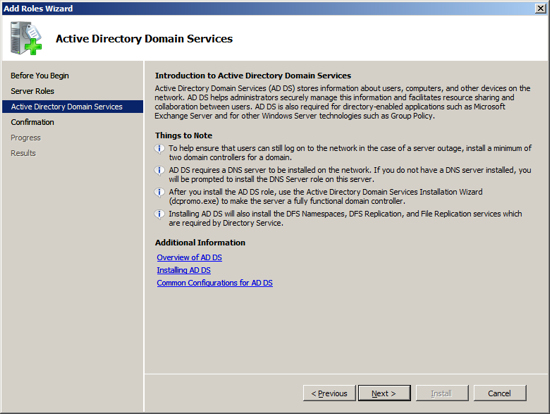
Now the installation will scan your configuration and inform you if
there are any pre-requisites that you have not fulfilled. If the
Active Directory Installation presents an errors, correct these at this
time and then repeat the installation. Once the Setup program
indicates that you have met all pre-requisites, then press the
Install button to start the installation process.
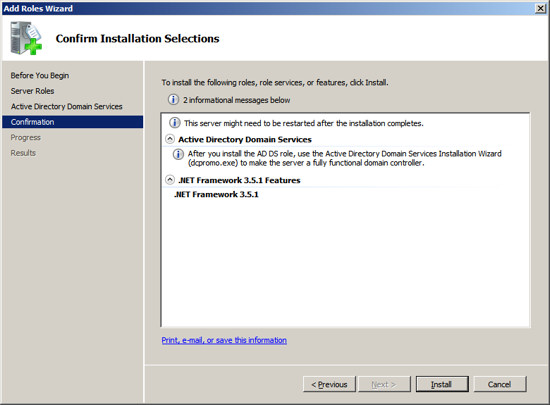
The setup program will now install Active Directory on your Server.
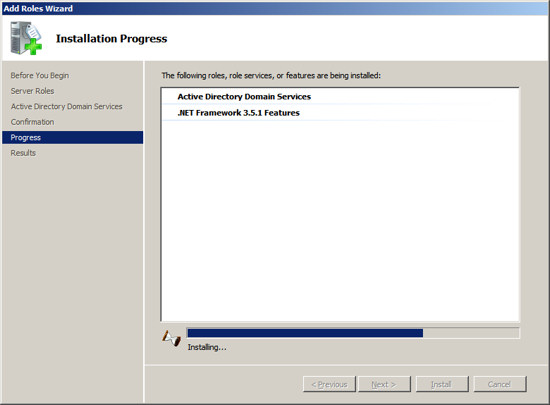
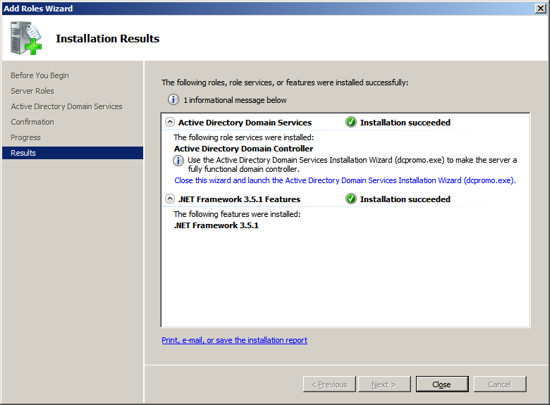
When the installation is complete, you should see a message indicating
"Installation Succeeded".
Press Close to return to the Server Management
Screen.
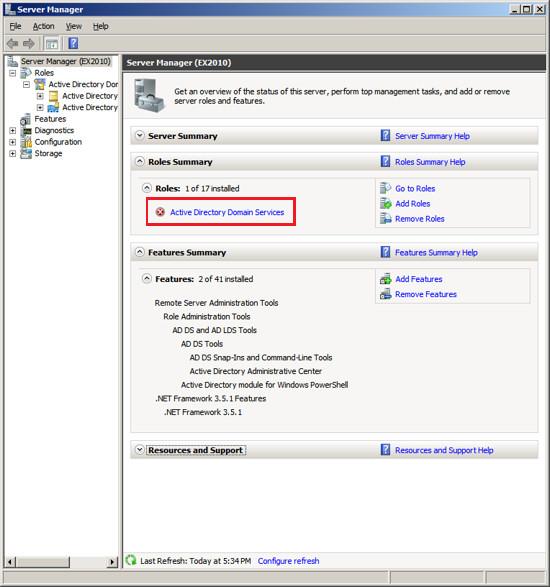
 Step 2 - Configure Active Directory
Step 2 - Configure Active Directory
At the Server Management screen you should now see that you have 1
role installed. The Active Directory Domain Services may indicate
that it is installed but there are errors. This is because the
software is installed but not configured.
To configure Active Directory, click on the line under Roles labeled
"Active Directory Domain Services". The Server Manager will show
you a page about the status of the Active Directory Role.
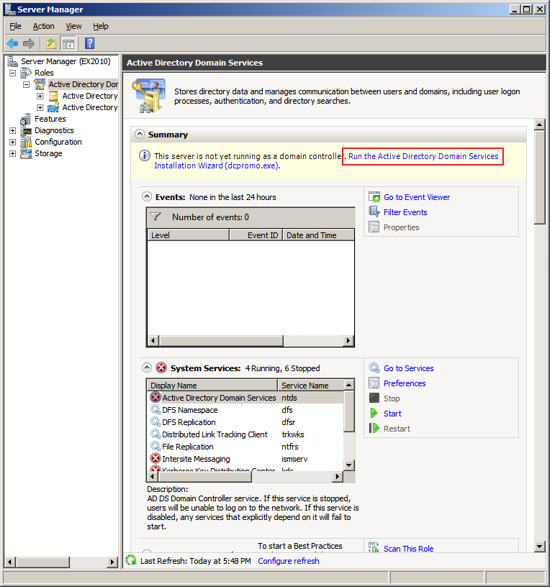
Click on the link "Run the Active Directory Services
Installation Wizard (dcpromo.exe)". When the
Active Directory Domain Services Installation Wizard appears, press
Next.
The Installation Wizard will present information about the version of
Active directory, press Next.
Since we are assuming this Exchange Server will be the first Domain
Controller, we choose "create a new domain in a new forest". Press
Next.
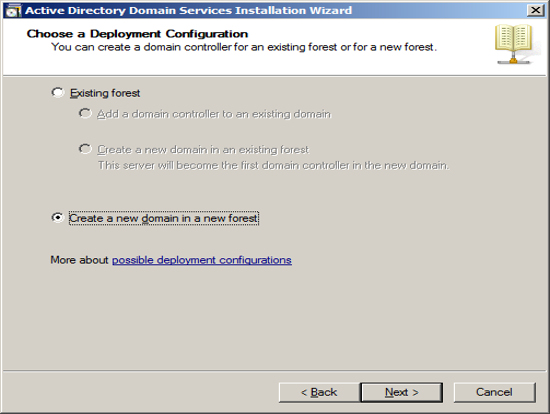
Enter the name of your domain. The domain name you enter here
is the domain name that Exchange will associated with all of your email.
If you use a hosting company to host your Internet Domain, then you may
want to enter the name of your Internet domain with ".local". If
you host your own Internet Domain then you would enter your domain name
here.
In our example, we are assuming that IGetMail.com is hosted at an
Internet Hosting Company. Since we do not host IGetMail.com on
this Exchange Server, we will use IGetMail.local to indicate our
internal domain for IGetMail.
NOTE: Once you enter your domain name it is very hard to change
it in the future, so you should take great care when enter this name.
Once you have decided on the name of your internal domain, that will
be your Active Directory Domain and the domain serviced by Exchange,
press Next.
The Installation Wizard will now ask you about compatibility.
If you plan to have domain controllers running various versions of
Active Directory, then you will want to chose a function level to include
the lowest version of Windows that you are using for domain controllers.
Press Next.
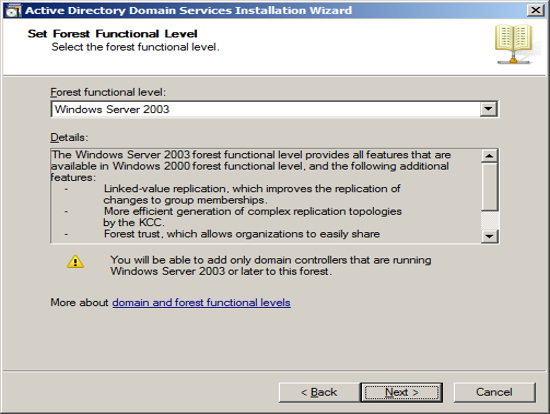
You will be asked a similar question which is at the domain
level instead of the forest level on the previous screen. You
should follow the same approach and include the function level to
include the lowest version of Windows you plan to use for domain
controllers. Press Next.
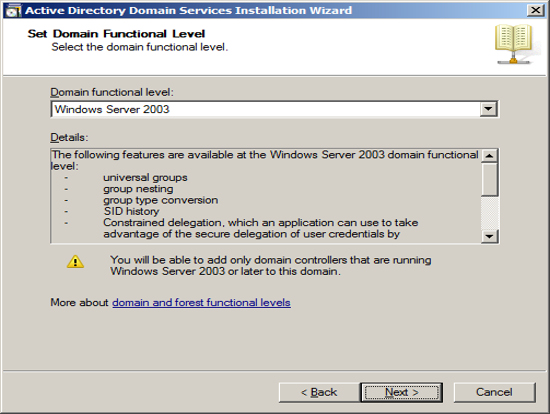
The first Domain Controller needs to have a DNS server running
locally. The optimal location is to start out with having the
installation wizard install the DNS server locally. Also, it will
automatically make this computer a global catalog server. Press
Next.
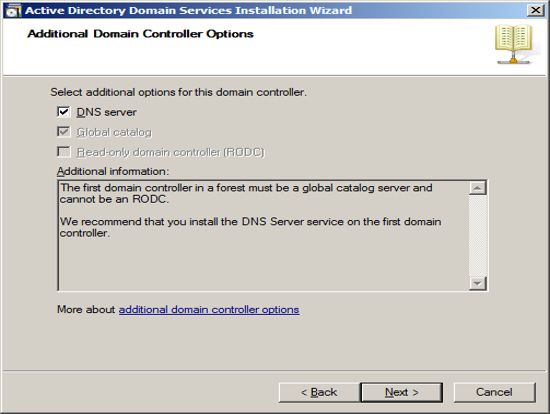
You can specify where you want Active Directory to store its data.
If you only have one drive in your Server, then use the defaults.
If you have multiple drives, you can select which drive to use.
Press Next.
Should you need to restore Active Directory in the event of a hard
drive failure, you will need to boot your Server into a special mode
called "Directory Restoration Mode". Should you need to boot your
computer into this special mode, you will need to use a special password
just for this restoration. You can define this password at this
time.
NOTE: This password is different than the
administrator account and if you change the administrator password this
password will not change. So you will need to store this password
forever in a safe place. Press Next.
Now the Installation Wizard will summarize the configuration that it
is about to create. To start the process of configuring
your new Domain Controller, press Next.
The Installation Wizard will show its progress as it configures your
Server. This will take a long time.
When the installation is complete, you will be shown a final screen.
Press Finish.
Then restart your computer.
After restarting your computer, Windows should show you the Server
Manager. You should see on the Server Manager screen that you have
Active Directory and DNS Server roles installed. Also the process
of installing Active Directory will add the features "Group Policy
Management" and "Remote Server Administration Tools".
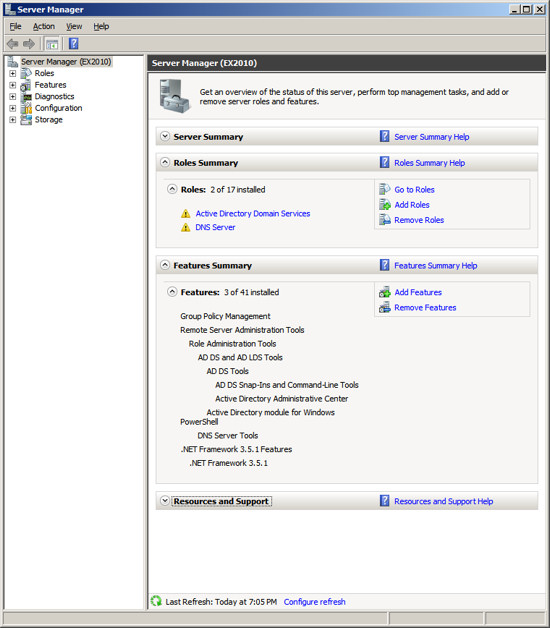 Add role - Active Directory Lightweight Services
Add role - Active Directory Lightweight Services
Now that have your Server configured for Active Directory, Exchange
requires that you add the Lightweight Service. NOTE: Exchange only
requires that the Lightweight services are installed. It does not
require the Lightweight Services to be configured.
Click on the link "Add Roles" and then select to add the role "Active
Directory Lightweight Directory Services" and press Next.
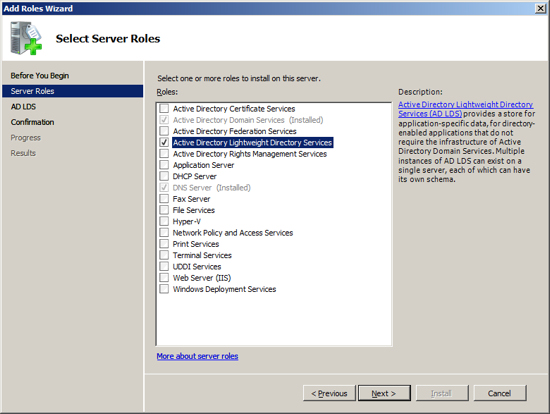
The installation wizard will inform you that it will make the
following modifications to your server. Press Next.
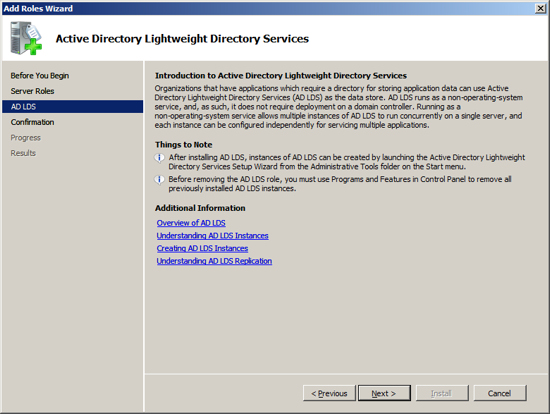
The installation wizard will confirm your intention, press
Install to begin.
The installation wizard will show its progress.
And finally when the role has been installed, the installation wizard
will show its results. Press Close and then proceed to configure
this newly installed role.
At this point your Server Manager should show you that you have the
Active Directory Lightweight Directory Services installed. This is
sufficient for Exchange. If you want to create LDS instances you
are welcome to, but that task is not required by Exchange.
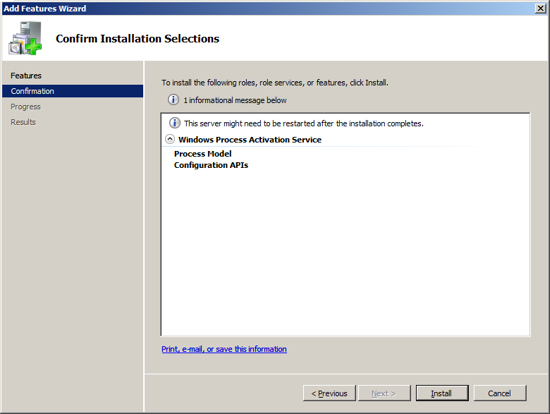
Add feature - Windows Process Activation Service
The next feature that Exchange needs installed is the "Windows
Process Activation Service". To install this feature, click on the
link "Add Features".
At the Select Features screen, check/tick the feature "Windows
Process Activation Service".
Select the items under this
service and press Next.
Confirm your selections and press Install. Windows will now
install this feature and when it is complete, press Close to return to
the Server Manager.
 Add role - Web Server (IIS)
Add role - Web Server (IIS)
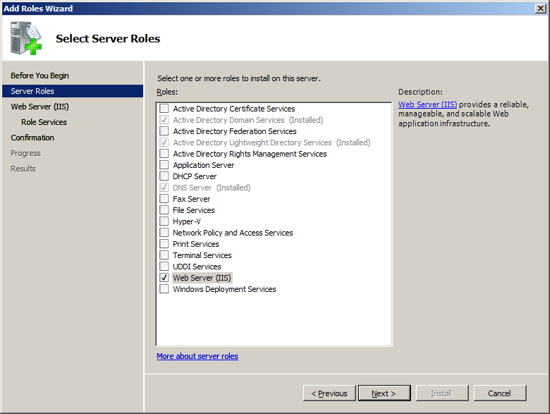
The next Role that Exchange needs installed is the Web Server IIS.
To install this role, at the Server Manager click on "Add Roles".
At the Select Server Roles screen, check/tick the role "Web Server (IIS)"
and press Next.
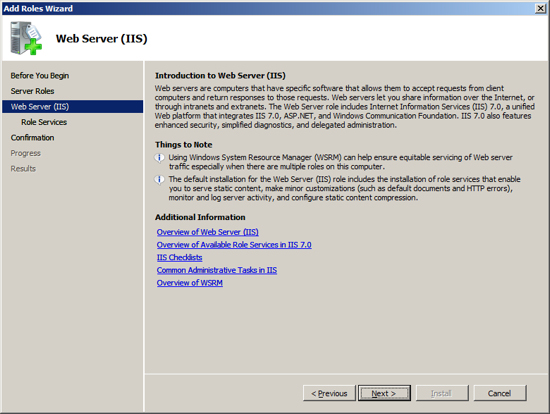
The Web Server IIS installation will present information about what
it will perform. Press Next.
Exchange requires that several additional services be added to the
default settings in IIS.
In addition to the default settings, check/tick the following additional services:
- Security - Basic Authentication
- Security - Windows Authentication
- Security - Digest Authentication
- Performance - Dynamic Content Compression
- Management Tools - IIS 6 Management Compatibility (include all
items under this service)
Press Next.
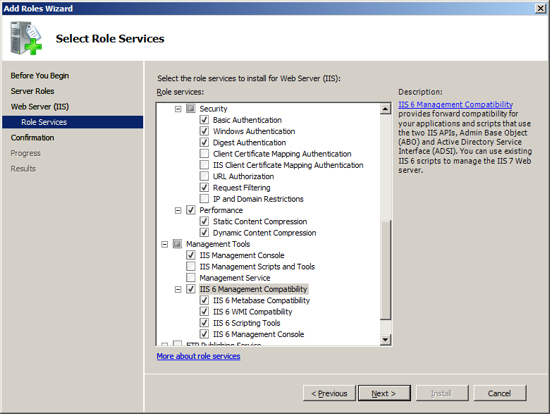
The Web Server installation wizard allows you to verify your
selections. Press Install to begin.

The installation wizard will now install IIS on your Exchange Server.
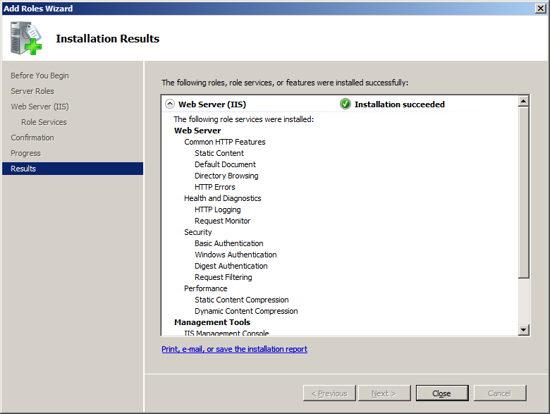
When IIS is installed, press Close to return to the Server Manager.
 Add feature - PowerShell
Add feature - PowerShell
Now you are ready to install the next feature that Exchange requires
as a prerequisite: "Windows Power Shell". At the Server Manager click on
the link "Add Feature".
Select the Feature "Windows Power Shell" and press Next.
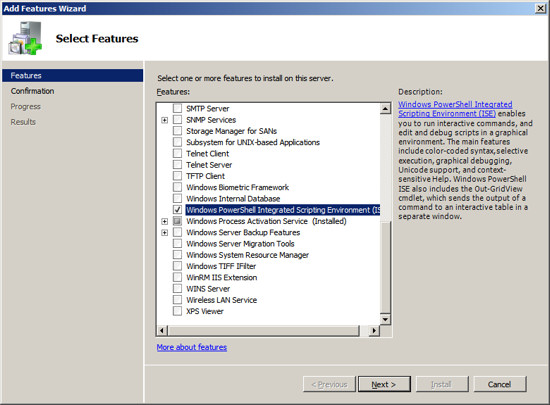
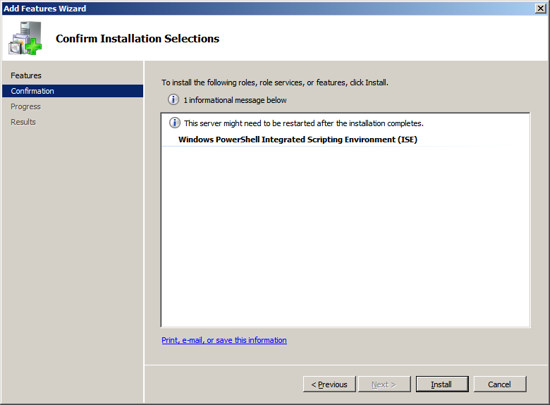
At the installation confirmation screen, press Install to begin the
process of installing this feature.
When the Power Shell feature
is installed, press Close to return to the Server Manager.
We have just 2 more items to meet Exchange's Requirements.
Enable TCP Port Sharing
When you install Windows Server 2008, the default setup disables a
service that is needed by Exchange. You will need to enable this
service.
At the Server Manager screen - expand "Configuration" in the left
hand panel. Then click on "Services". The middle of the
screen will show the installed Services. Scroll to the Service
named "Net.Tcp Port Sharing Service".
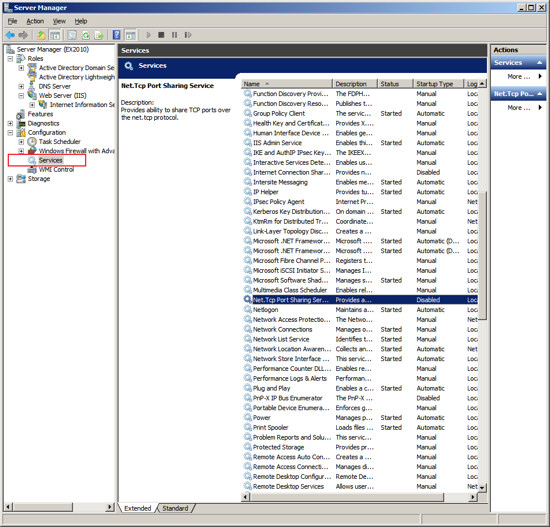
Right Click on the Service "Net. Tcp Port Sharing" and choose
Properties.
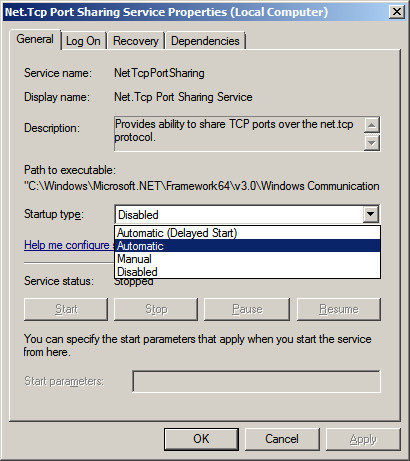
Change the Startup from Disabled to Automatic.
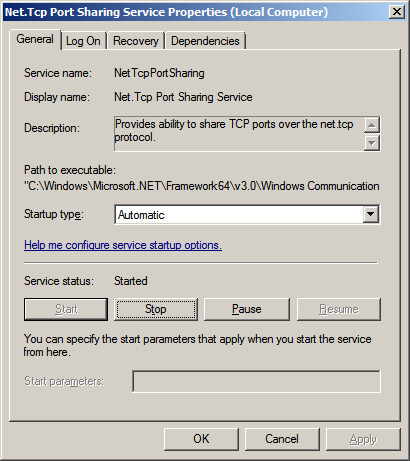
Press OK to save your changes.
Apply the 2007 Office System Converter
You will
need to download the 2007 Office System Converter Pack.
Click on this link to go to Microsoft's Download Site.
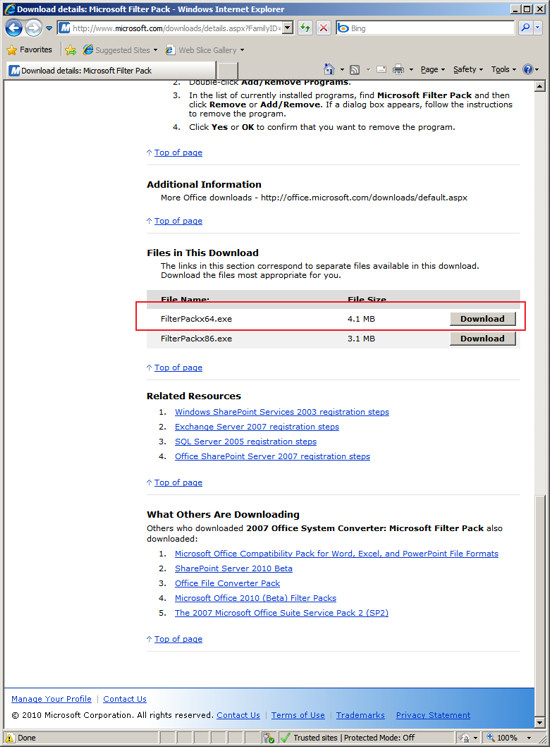
Click on the link "Download Files Below". Then press the
"Download" button
next to the File Name "FilterPackx64.exe".
Download and install the Filter Pack:
Press Next and proceed through the wizard.
When you have completed the Filter Pack installation you are now
ready to install Exchange 2010.
 Roles / Features NOT to install
Roles / Features NOT to install
Exchange has a requirement to use its own SMTP service and not the
SMTP Role that is built into Server 2008. As a result, you must
not
install the SMTP feature from the Server Manger. This will be
installed by Exchange. Note that the Exchange Setup wizard will
issue a warning that the SMTP services are not already installed, yet if
you install the Windows 2008 SMTP feature, the Exchange Setup will
consider that an error.
Installing Exchange Server 2010
You are now ready to install Exchange Server 2010.
When you run the Exchange Server setup, the first 2 steps have been
completed and will be inactive. The next step you need to perform
is to select the Language Option. Click on "Choose Exchange
Language Option".
Now select the language option that is appropriate for your environment.
After selecting your language option you are ready to being the
installation.
Click on the link "Install Microsoft Exchange."
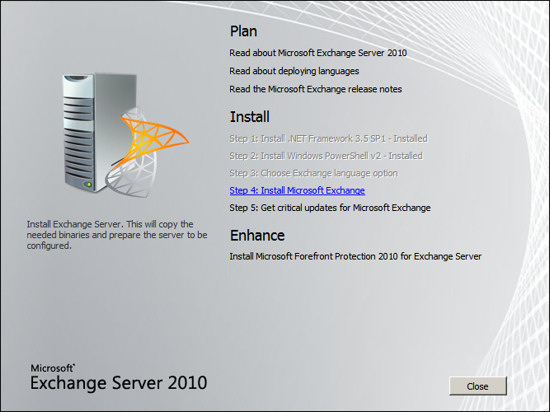
The Exchange Server 2010 setup wizard will present information about the
task it will perform, press Next.
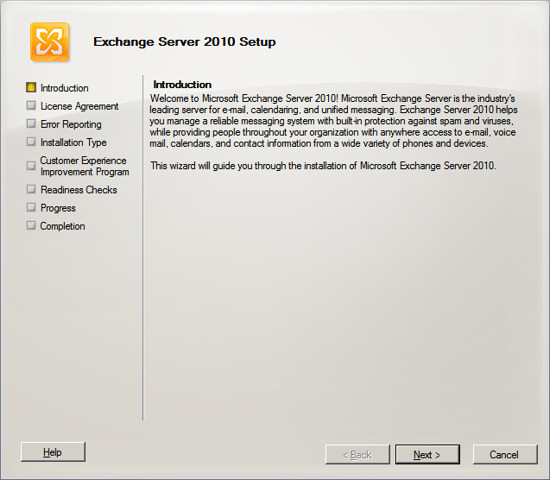
Accept the license agreement and press Next.
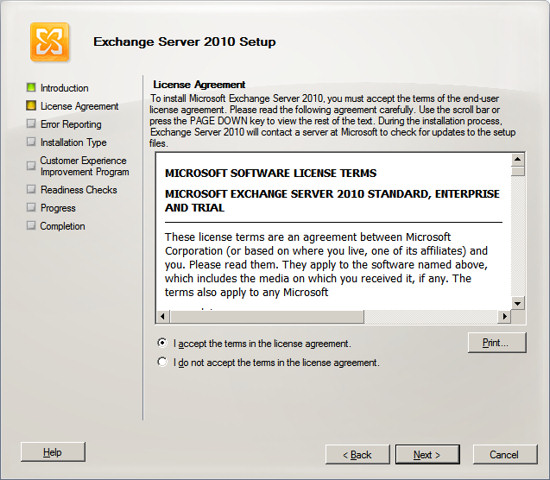
You can choose to participate in error reporting if you wish, press
Next.
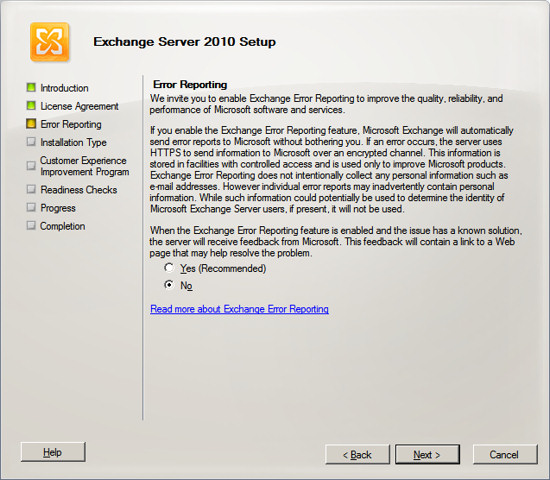
Since this is Exchange Server is intended to be our only Exchange server,
we will chose the typical installation which installs all of the
components to make this Exchange receive, store and send email.
Select "Typical Exchange Server Installation" and press Next.
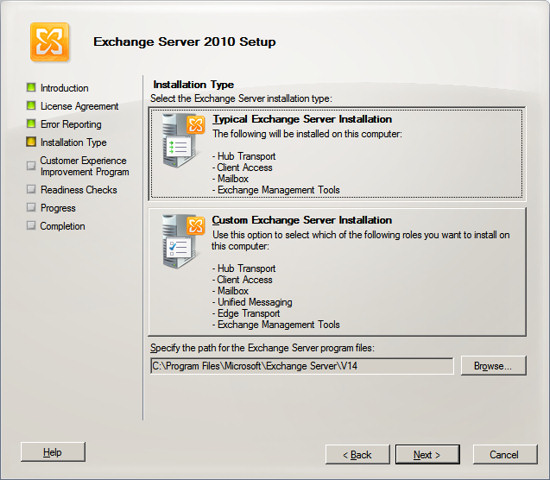
Enter the name of your organization, typically this corresponds to your
company name or domain name. Press Next.
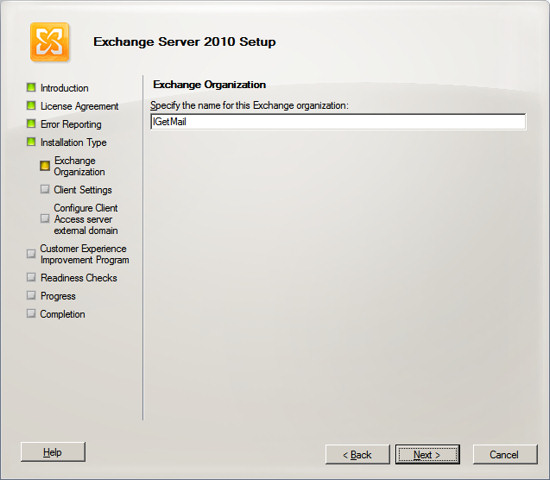
If you intend to use Outlook 2003 clients to connect to this Exchange
Server, then chose Yes to provide compatibility with these clients, then
press Next.
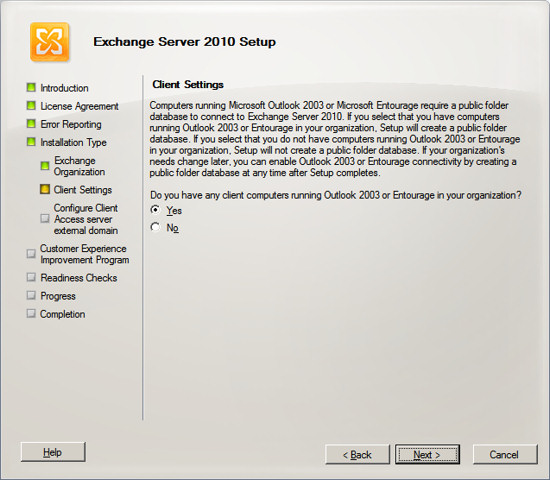
Exchange will now ask what you want to specify for the Internet
facing side of Exchange. In our example, using IGetMail we would
create the Internet facing side of Exchange as mail.igetmail.com.
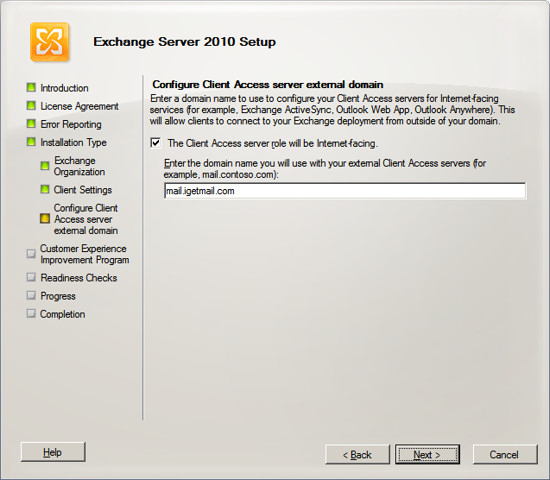
Next Exchange Setup will ask if you want to join the Customer
Experience Program.
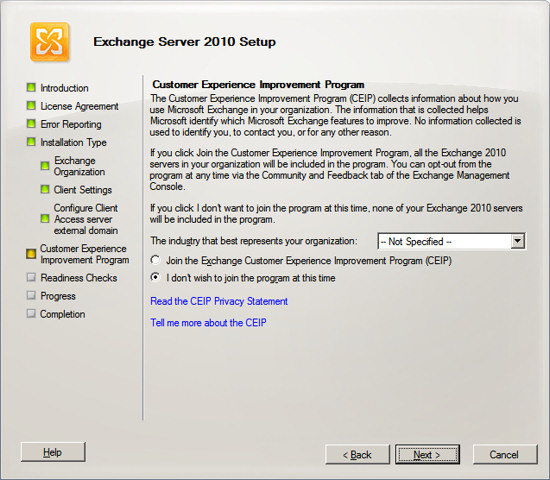
Exchange will now verify that all prerequisites are met. If
there are any items that Exchange needs, it will inform you at this
time. If the prerequisites have all been met, then press Install
to begin the installation.
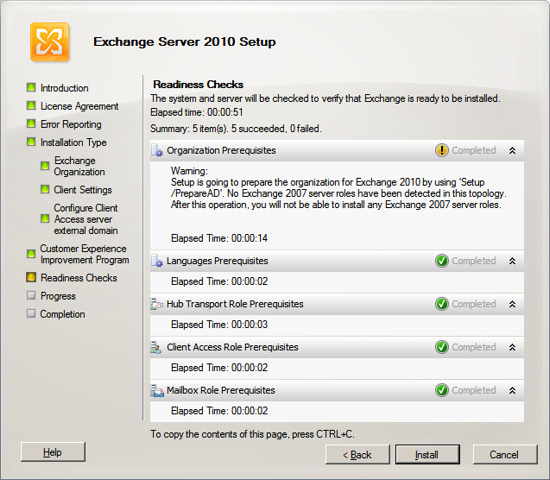
When the Exchange Server 2010 installation wizard completes, it will
show the results of installing each component within Exchange Server.
You should see all components with a green check mark.
Press
Finish and your Exchange Server should now be ready to use.
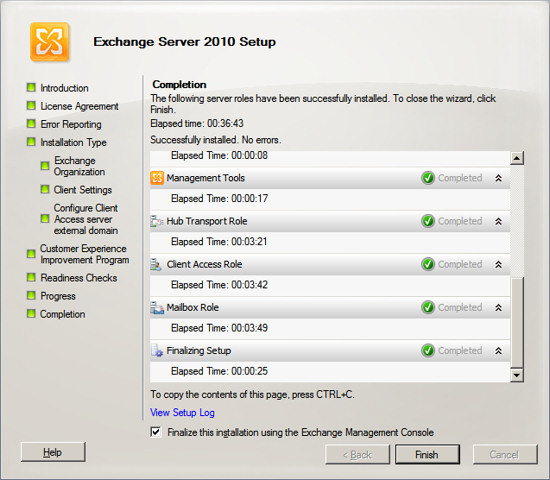
When Exchange completes its installation, the Exchange System Manager
will appear. The Exchange System Manager will guide you through
several post installation tasks.
 Allow IGetMail access to your Exchange Server
IGetMail Version 3.x instructions:
Allow IGetMail access to your Exchange Server
IGetMail Version 3.x instructions:
When you are running IGetMail version 3.x you can instruct IGetMail
to send email to your Exchange
server using an
authenticated user
or
anonymous access.
Authenticated User Access - With this method you instruct IGetMail to
use a specific Exchange user account to connect to the Exchange Server.
Once connected through this account, IGetMail can send email to any of
your Exchange user accounts. In order to use this method, the
Exchange user account must be a member of the Exchange Server Group
within Active Directory.
To setup Authenticated Access:
- Open the Exchange Management Console
- Expand "Server Configuration"
- Select "Hub Transport"
- In the middle section of the Management Console you will see the
list of Receive Connectors.
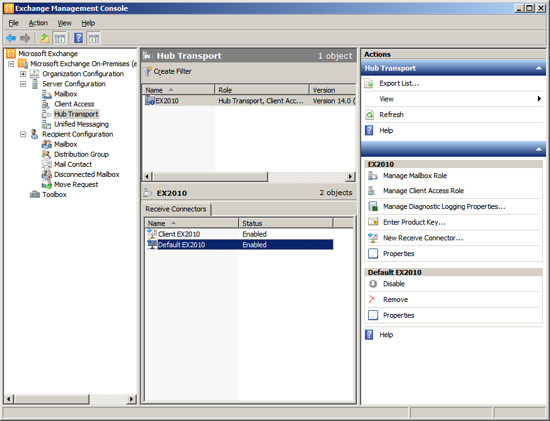
- Right click on the Receive Connector "Default ServerName" and
choose Properties
- Select the "Authentication" tab.
- If you do not have an SSL certificate from a third party SSL
provider, then Uncheck / Untick the option "Offer Basic
authentication only after starting TLS". By default Exchange
will not allow users to authenticate until you have an SSL
certificate. Unchecking / Unticking "Offer Basic
authentication only after starting TLS," allows Exchange to offer
Authenticated login over standard SMTP.
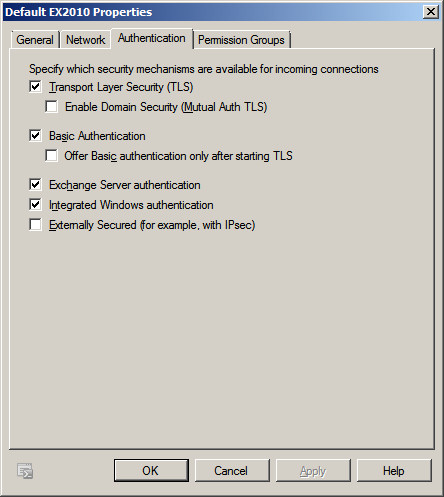
When you configure IGetMail, you will need to specify a Windows user
that meets these two requirements.
- The Windows account must have a mailbox in Exchange
- The Windows user must be a member of the group "Exchange
Servers"
Commonly, the Administrator account does not work because it does not
have a mailbox and a standard Windows account is normally not a member
of the Exchange Server group. To solve this you can either give
the administrator a mailbox, or in our example below we created a Windows
user, made this Windows user a member of the "Exchange Servers" groups,
and then created a mailbox for the user. In our example this new
Windows user is named "IGetMail".
- Run Active Directory for Users and Computers.
- Select the Users group in the column on the left.
- Right Click and add a new user. In our case we choose to
name this new user "IGetMail" since we will use this Windows user
account to route the email through as the email is delivered to all
of the other users within Exchange.
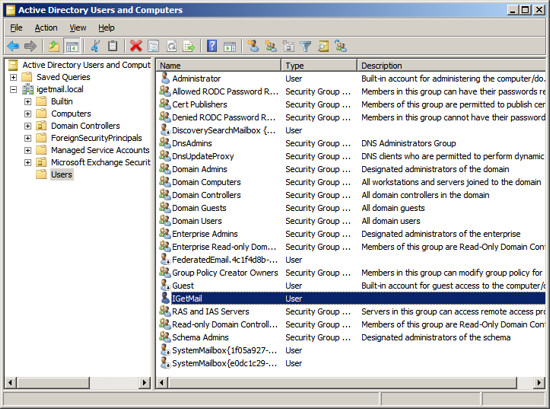
- Select the Window user account that you want to have IGetMail
use to connect to your Exchange Server. Right click on the
user name and choose Properties.
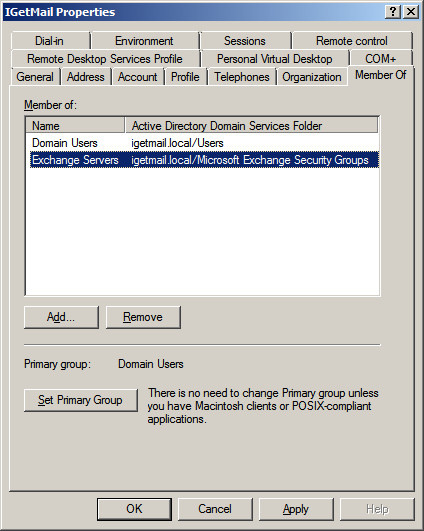
- Go to the "Member Of" panel.
- Press the Add... button.
- Add the Group "Exchange Servers" to make this Windows account a
member of the "Exchange Servers" group. This will grant this
Windows account the rights to route email to other users. This
is needed for IGetMail to route email to your users.
Next we need to add a mailbox to the Windows account that IGetMail
will use for authentication.
- Run the Exchange Management Console
- Expand "Recipient Configuration"
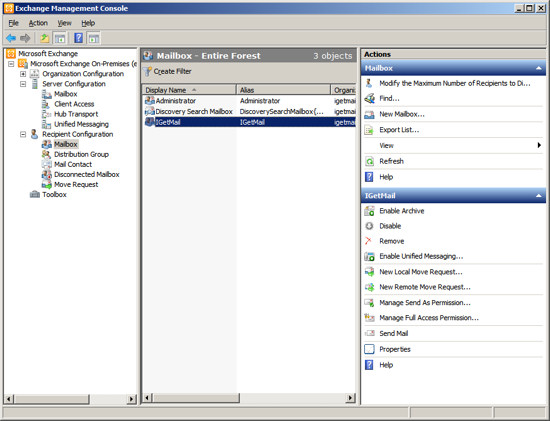
- Select Mailbox to show a list of existing Exchange Users
- Right Click on "Mailbox" under "Recipient Configuration" and
select New Mailbox or Click on New Mailbox in the Actions Column on
the right hand side.
- Add the Windows account that you want IGetMail to use to the
list of Exchange users. In our example below we have added the
account "IGetMail" to the list of Exchange Users.
Now Run IGetMail
- At the Status Panel, press the "Modify SMTP Settings" button.
- Check / Tick the option "Authenticate as - "
- Enter the Name of a Windows User Name that you want IGetMail to
use to connect to the Exchange Server. This Windows account
must have a mailbox in Exchange and must be a member of the
"Exchange Servers" group.
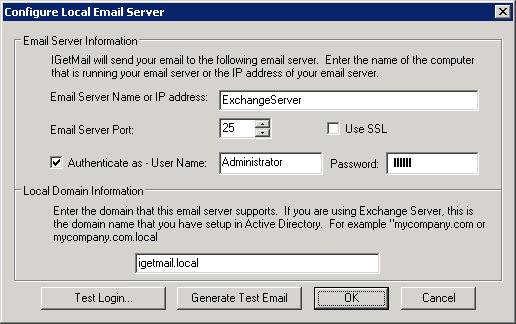
IGetMail is now configured to send email to your Exchange Server.
To Setup Anonymous Access:
Anonymous access - With anonymous access you can allow anyone to send
email to any of your users. In this case, IGetMail only has to
connect to the Exchange Server. It does not need to log into a Windows
Account.
To configure Exchange to allow any user to route email perform these
steps:
- Open the Exchange Management Console
- Expand "Server Configuration"
- Select "Hub Transport"
- In the middle section of the Management Console you will see the
list of Receive Connectors

- Right click on the Receive Connector "Default ServerName" and
choose Properties
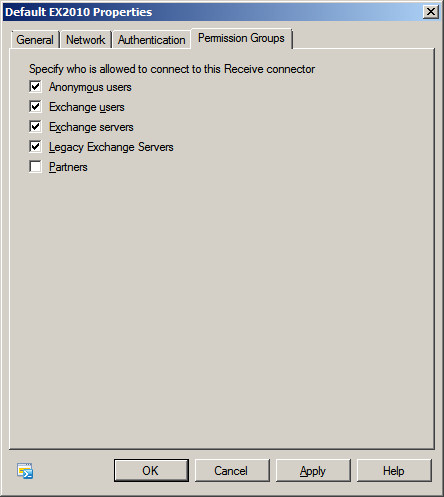
- Select the "Permissions Group" tab
- Check / Tick "Anonymous Users"
- Save your changes
- Now anyone can connect to the Exchange Server and route email to
any user
 IGetMail Version 1.x and 2.x instructions:
IGetMail Version 1.x and 2.x instructions:
When you are running IGetMail Version 2.x and 1.x you need to allow
anonymous SMTP connections for your server.
Method 1 - Run the Exchange Management Console. Expand the
Server Configuration and select Hub transport. In the lower half
of the screen under the tab "Receive Connectors" right click on the
connect labeled "Default <Name Of Your Server>" and select Properties.
At the Properties for the default server select the Permissions Group
tab. At the Permissions Group Tab, check / tick the option
Anonymous and save your changes.
Method 2 - Run the following management shell command (note this is
the Exchange Management shell and not the PowerShell):
Set-ReceiveConnector -Identity "Default <ServerName>" -PermissionGroups "AnonymousUsers"
Where you would replace <ServerName> with the computer name of this
server.
Adding E-Mail Users
Run the Exchange Management Console. Expand the item
"Recipient Configuration" and select Mailbox.

Click on the option "New Mailbox" in the right hand panel under the
Actions column heading.
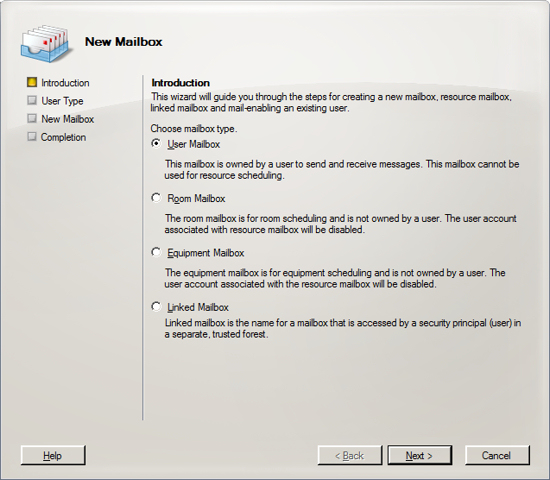
Proceed through the wizard to create each of your new users.